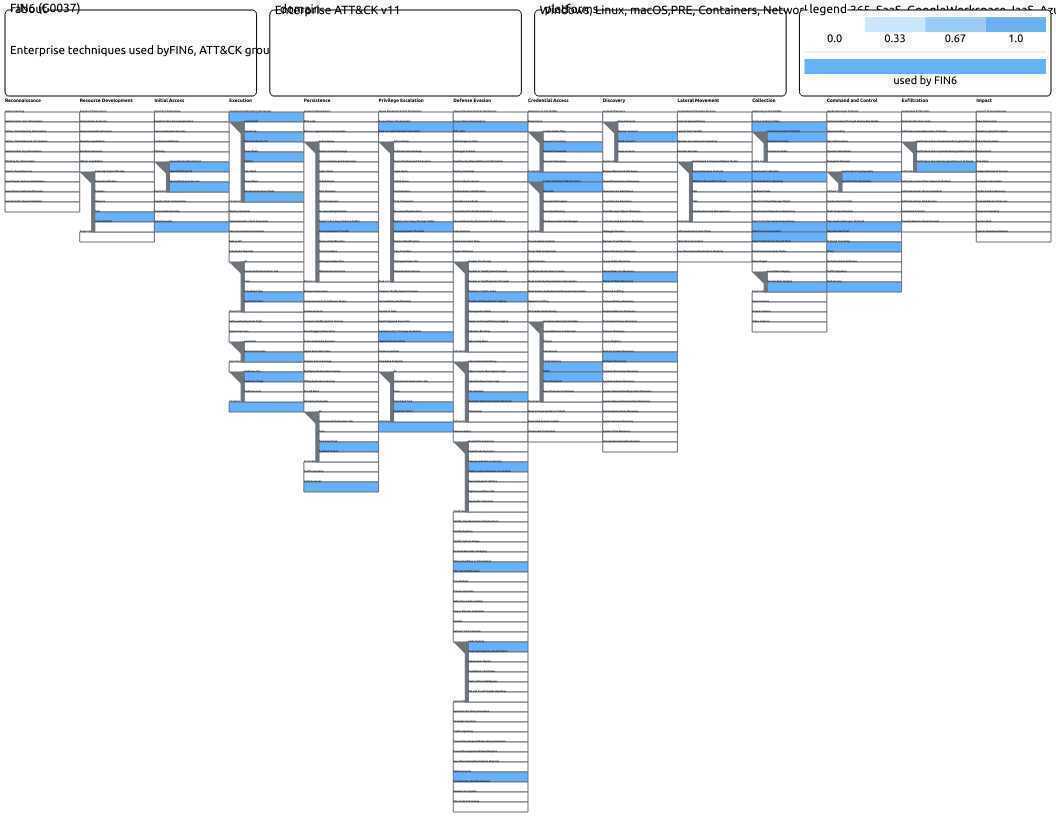
Real-World Adversary Behaviours
We emulate adversary behaviours through specific tactics, techniques and procedures (TTPs) of groups that would target your organisation’s industry and profile, so that you can verify organisational processes, ensure tooling is performing as expected and to provide opportunities for your people to practice their response.


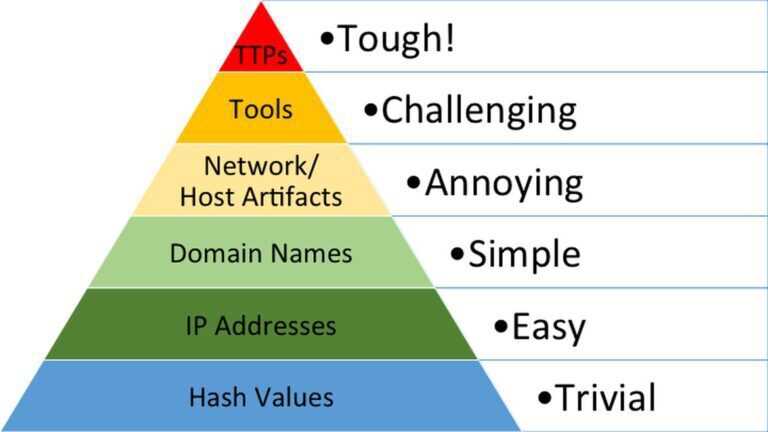 Pyramid of Pain by David Bianco
Pyramid of Pain by David Bianco